In today’s interconnected world, the adoption of remote access solutions for Industrial Control Systems (ICS) has grown exponentially. While this advancement enhances operational efficiency and flexibility, it also introduces a myriad of cybersecurity challenges. Ensuring the secure remote access of ICS is paramount to protecting critical infrastructure from cyber threats.
Key Challenges in ICS Remote Access Security
Remote access to ICS environments opens a pathway for cybercriminals to exploit vulnerabilities. Common challenges include insufficient authentication mechanisms, outdated software, and insecure remote desktop protocols. Additionally, the lack of network segmentation often allows attackers to move laterally within the system once access is gained. Addressing these challenges requires a comprehensive understanding of ICS-specific risks and a proactive security approach.
Best Practices for Secure Remote Access
- Implement Multi-Factor Authentication (MFA): Adding an extra layer of security ensures that unauthorized users cannot access ICS, even if credentials are compromised.
- Use Virtual Private Networks (VPNs): Securely encrypt communications between remote users and the ICS network, reducing the risk of data interception.
- Adopt Zero-Trust Architecture: Continuously verify the identity and trustworthiness of users and devices before granting access.
- Apply Strict Access Controls: Limit access to ICS components based on roles and responsibilities to minimize exposure.
- Regularly Update and Patch Systems: Keeping software and hardware up-to-date helps prevent exploitation of known vulnerabilities.
Role of Network Segmentation
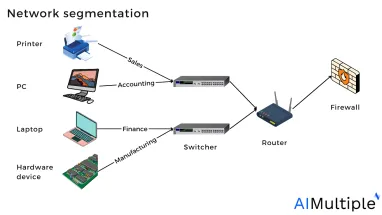
Network segmentation is a critical strategy in securing ICS environments. By isolating ICS components from the broader corporate network, organizations can limit the potential impact of an intrusion. Proper segmentation ensures that even if one segment is compromised, attackers cannot easily access other parts of the network.
Monitoring and Incident Response

Continuous monitoring of ICS networks for unusual activity is vital. Advanced threat detection systems can identify and mitigate breaches in real-time. Additionally, having a robust incident response plan tailored to ICS environments ensures quick recovery and minimizes downtime in the event of a cybersecurity incident.
The Future of ICS Security

As industrial operations embrace digital transformation, securing remote access will remain a top priority. Emerging technologies, such as artificial intelligence and machine learning, are poised to enhance threat detection and response capabilities. Organizations must stay informed about evolving threats and invest in ongoing training and security enhancements to safeguard their ICS environments.