As quantum computing progresses, its implications for encryption—the backbone of digital security—have become a pressing concern. Encryption protocols, designed to protect sensitive data from unauthorized access, face a formidable challenge from quantum computers’ unparalleled processing power. But what exactly is the impact of quantum computing on encryption, and are we prepared to defend against it?
What Is Quantum Computing?

Quantum computing is an advanced field of computation that leverages the principles of quantum mechanics. Unlike classical computers, which process information as binary bits (0s and 1s), quantum computers use qubits.
- Unique Properties of Qubits:
- Superposition: Qubits can represent both 0 and 1 simultaneously, increasing computational power exponentially.
- Entanglement: Qubits can correlate with one another, enabling faster and more complex calculations.
These properties allow quantum computers to solve problems that would take classical computers millennia, including breaking traditional cryptographic systems.
How Does Encryption Work Today?
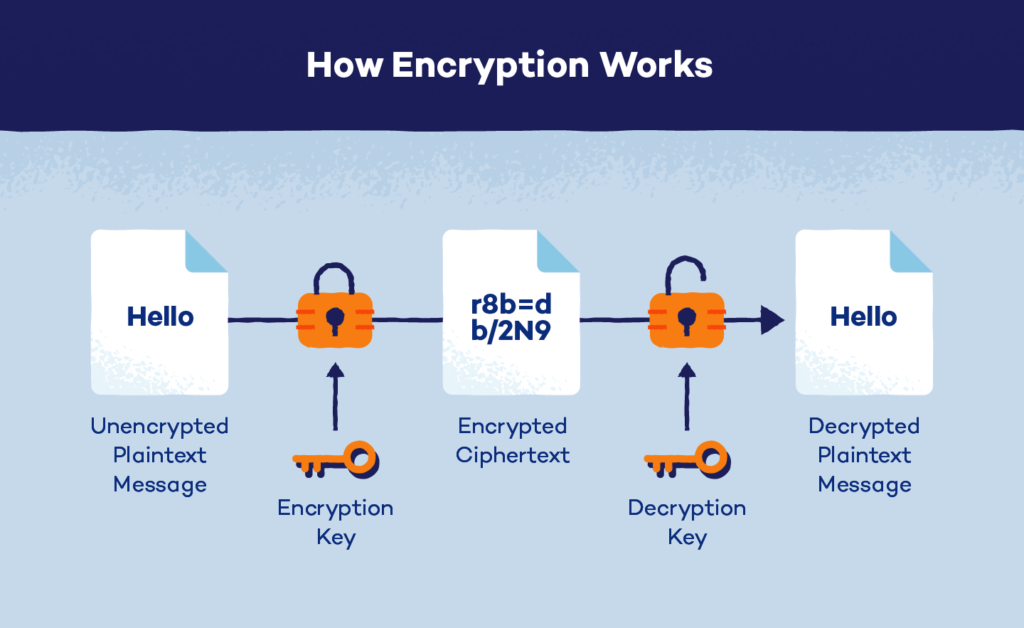
Modern encryption methods rely on mathematical problems that are infeasible for classical computers to solve within a reasonable timeframe.
- Symmetric Encryption: Uses a single key for encryption and decryption (e.g., AES).
- Asymmetric Encryption: Uses a pair of keys—a public key for encryption and a private key for decryption (e.g., RSA, ECC).
The security of asymmetric encryption, in particular, depends on the computational difficulty of tasks like factoring large prime numbers (RSA) or solving discrete logarithms (ECC). Quantum computing threatens to upend these assumptions.
Quantum Computing’s Threat to Encryption
Quantum computers can potentially render current encryption obsolete by leveraging algorithms designed to solve mathematical problems exponentially faster.
- Shor’s Algorithm: Efficiently factors large integers, breaking RSA encryption.
- Grover’s Algorithm: Reduces the brute-force search space for symmetric encryption by half, undermining AES’s security margins.

While symmetric encryption can be fortified by doubling key lengths, asymmetric encryption faces a more existential threat, requiring entirely new cryptographic methods.
The Urgency of the Post-Quantum Era
The “post-quantum era” refers to the time when quantum computers become powerful enough to break existing cryptographic systems. Experts predict this could happen within the next 10–20 years, although recent advancements suggest it might arrive sooner.
- Potential Risks:
- Data Theft: Cybercriminals could intercept encrypted data today and decrypt it once quantum computers become viable.
- Infrastructure Vulnerabilities: Critical systems like financial institutions, healthcare networks, and military operations are at risk.
- Loss of Privacy: Sensitive personal and corporate data could be exposed, undermining trust in digital systems.
Are We Ready for Quantum Computing’s Impact on Encryption?
Preparation for the quantum threat requires proactive measures, including the development and adoption of post-quantum cryptography (PQC).
- Post-Quantum Cryptography: Refers to cryptographic algorithms designed to resist quantum attacks while remaining secure against classical threats.
- Examples of PQC Algorithms: Lattice-based cryptography, code-based cryptography, multivariate polynomial cryptography, and hash-based signatures.
In 2022, the National Institute of Standards and Technology (NIST) announced the first standards for post-quantum cryptography, signaling global recognition of the need for transition.
Steps Toward Post-Quantum Readiness

Organizations and governments must begin transitioning to quantum-resistant cryptographic systems to safeguard against future threats.
- Risk Assessment: Identify critical systems and data at risk from quantum attacks.
- Inventory Management: Audit cryptographic systems to evaluate their vulnerability.
- Hybrid Cryptography: Combine classical and post-quantum algorithms to ensure a smooth transition.
- Collaboration: Work with industry peers and government bodies to share knowledge and standardize PQC practices.
- Regular Updates: Stay informed about advancements in quantum computing and cryptographic standards.
Future-Proofing Encryption Technologies
Innovations in cryptography are not limited to post-quantum algorithms. Researchers are also exploring alternative approaches to secure data in a quantum-powered world.
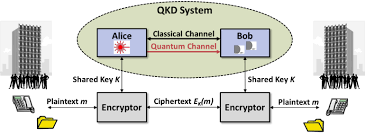
- Quantum Key Distribution (QKD): Uses quantum mechanics to securely distribute encryption keys, making them immune to interception.
- Homomorphic Encryption: Allows computations on encrypted data without decrypting it, enhancing security in cloud environments.
- Blockchain Integration: Ensures data integrity and transparency, even in quantum-adversarial environments.
The impact of quantum computing on encryption is both a challenge and an opportunity to innovate. As the post-quantum era approaches, the urgency to adopt quantum-resistant cryptographic methods cannot be overstated. Organizations, governments, and cryptographers must collaborate to develop resilient systems that can withstand both classical and quantum threats.
By prioritizing research, implementation, and awareness, we can secure our digital infrastructure and ensure that data privacy and integrity remain intact in a quantum-powered future.
FAQs
What makes quantum computing a threat to encryption?
Quantum computers can solve complex mathematical problems, like factoring large numbers, far faster than classical computers, rendering current encryption methods vulnerable.
When will quantum computers break existing encryption?
Experts estimate this could happen within 10–20 years, but rapid advancements suggest it might occur sooner.
What is post-quantum cryptography?
Post-quantum cryptography refers to algorithms designed to resist attacks from both classical and quantum computers.
How can organizations prepare for the quantum threat?
Organizations should assess risks, transition to post-quantum algorithms, and adopt hybrid cryptographic systems to ensure continuity.
What is quantum key distribution (QKD)?
QKD uses quantum principles to distribute encryption keys securely, ensuring they cannot be intercepted or compromised.
Are symmetric encryption methods safe from quantum threats?
Symmetric encryption can be strengthened by using longer keys, but they are still susceptible to quantum-powered brute force attacks.