Cloud computing has revolutionized how businesses operate, offering unprecedented scalability, flexibility, and cost efficiency. However, as the cloud becomes central to digital infrastructure, cybercriminals are increasingly exploiting vulnerabilities in these systems. In 2025, these threats are more sophisticated than ever, putting sensitive data and business operations at significant risk.
Understanding these evolving threats is crucial for businesses to stay ahead in the cybersecurity race. This article delves into the top cyber threats exploiting cloud vulnerabilities, their impact, and strategies for mitigating them effectively.
The Rise of Cyber Threats in Cloud Environments
Cloud adoption continues to grow at a staggering rate. With this growth, cyber attackers are focusing their efforts on exploiting cloud-specific vulnerabilities. The shared responsibility model of cloud security often creates confusion, leaving gaps for attackers to exploit. Businesses increasingly find themselves targeted by advanced persistent threats (APTs), ransomware, and supply chain attacks tailored for cloud environments.
Major Cyber Threats Exploiting Cloud Vulnerabilities in 2025
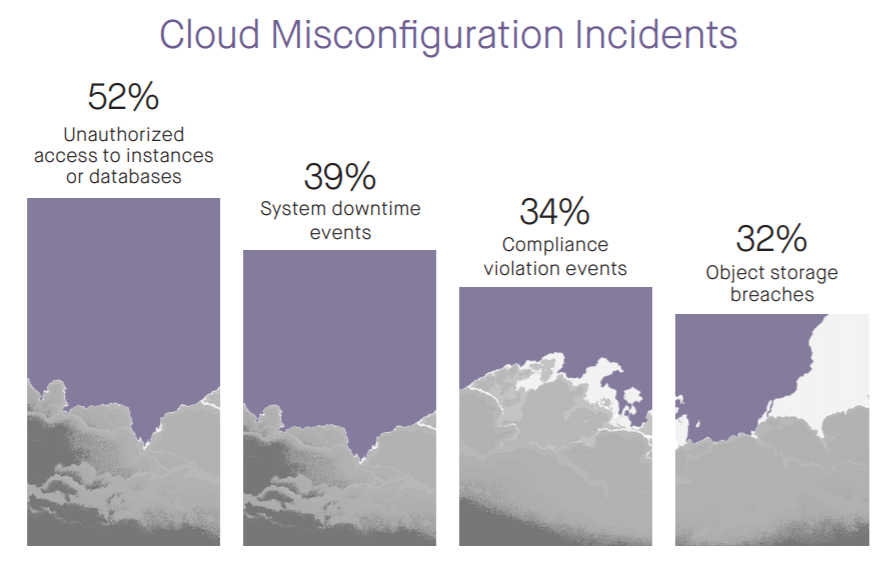
1. Misconfigured Cloud Resources
Misconfigurations remain one of the most common and damaging vulnerabilities in cloud environments. In 2025, attackers are leveraging AI-powered tools to scan for misconfigured storage buckets, databases, and other resources, exposing sensitive data.
2. Cloud Ransomware Attacks

Ransomware has evolved into a major menace, with attackers now targeting cloud systems to encrypt data stored across distributed architectures. Multi-cloud setups, often lacking cohesive security protocols, are particularly vulnerable.
3. Identity and Access Management (IAM) Exploitation

Weak or poorly configured IAM policies allow attackers to gain unauthorized access. Credential theft, privilege escalation, and session hijacking remain prevalent. Attackers increasingly exploit single sign-on (SSO) mechanisms, posing significant threats.
4. API Attacks

Cloud services rely heavily on APIs for communication. Vulnerable APIs are a prime target for attackers seeking to disrupt services, steal data, or inject malicious payloads. The rise of open APIs has expanded the attack surface, leading to a surge in API-based exploits.
5. Supply Chain Attacks in the Cloud
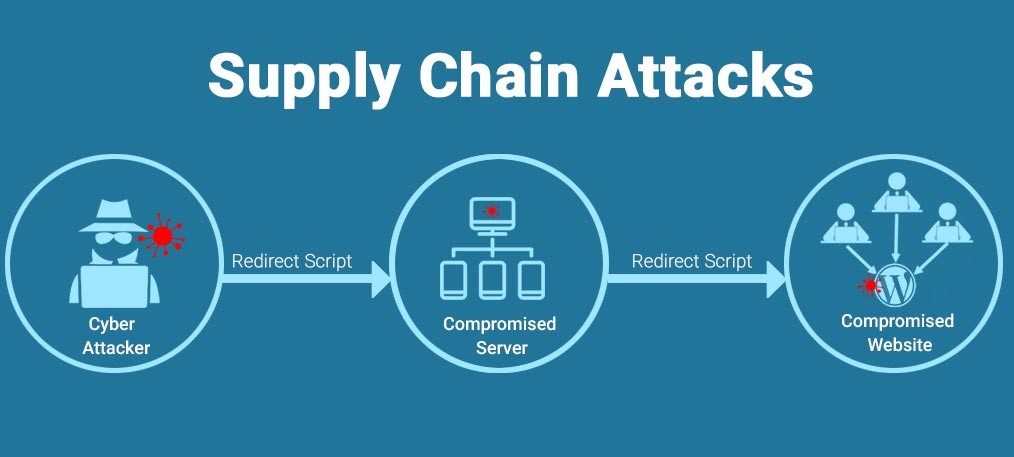
Cloud providers depend on third-party software and integrations, making them susceptible to supply chain attacks. Malicious actors inject compromised code into widely used software packages, enabling access to sensitive systems.
Emerging Trends in Cloud Cybersecurity Threats
AI-Powered Attacks

Cybercriminals are harnessing AI to automate attacks, bypass defenses, and identify vulnerabilities faster. AI is also used for phishing campaigns targeting cloud administrators.
Quantum Computing Threats

Though still nascent, advancements in quantum computing pose a looming threat to traditional encryption methods, potentially compromising cloud-stored data.
Zero-Day Vulnerabilities in Cloud Services
Zero-day exploits in popular cloud platforms are rising. Attackers are quick to exploit these unknown vulnerabilities before patches are released, leaving businesses defenseless.
Data Exfiltration in Hybrid Cloud Environments
Hybrid clouds, combining public and private cloud elements, are becoming a popular target for data exfiltration due to inconsistent security measures across platforms.
How to Mitigate Cyber Threats in Cloud Environments
1. Implement Robust IAM Practices
- Enforce multi-factor authentication (MFA) for all users.
- Regularly review and update IAM policies to limit privileges.
- Monitor login activities for unusual patterns.
2. Strengthen Cloud Configuration Security
- Use automated tools to identify and fix misconfigurations.
- Regularly audit cloud resources for compliance with security best practices.
- Encrypt data both in transit and at rest.
3. Secure APIs
- Adopt a “zero-trust” approach for API access.
- Regularly test APIs for vulnerabilities using penetration testing tools.
- Implement rate limiting and authentication measures for APIs.
4. Regularly Update and Patch Systems
- Maintain a rigorous patch management program for all software, including third-party integrations.
- Monitor for newly disclosed vulnerabilities and act promptly.
5. Invest in Threat Intelligence and Monitoring
- Use cloud-native security tools to monitor and detect threats in real-time.
- Leverage AI-driven threat intelligence systems for predictive insights.
6. Educate and Train Employees
- Conduct regular cybersecurity training for employees to recognize phishing attempts and other threats.
- Promote a culture of security awareness across the organization.
FAQs
What are the top cloud vulnerabilities in 2025?
Misconfigured resources, weak IAM policies, vulnerable APIs, and supply chain risks are some of the top cloud vulnerabilities in 2025.
Why are ransomware attacks targeting cloud systems?
Ransomware attacks target cloud systems due to their centralized data repositories, offering attackers significant leverage over businesses.
How can businesses protect their cloud environments from API attacks?
Businesses can protect against API attacks by implementing zero-trust models, conducting regular penetration testing, and using strong authentication methods.
What role does AI play in cloud cybersecurity?
AI helps automate threat detection, identify vulnerabilities, and respond to attacks faster. However, it also enables attackers to create more sophisticated threats.
Are hybrid clouds more vulnerable to cyber threats?
Hybrid clouds can be more vulnerable due to inconsistent security measures across public and private components. Proper configuration and monitoring are essential.
What is the shared responsibility model in cloud security?
The shared responsibility model delineates security obligations between cloud providers and users. Providers manage the infrastructure, while users are responsible for data and configurations.
Cyber threats targeting cloud vulnerabilities are becoming increasingly sophisticated in 2025, driven by advancements in technology and the growing reliance on cloud services. Businesses must adopt proactive security measures, leverage cutting-edge tools, and foster a culture of cybersecurity awareness to protect their digital assets effectively. By staying informed and prepared, organizations can mitigate risks and ensure the security of their cloud environments.